Encryption is the process of transforming data so only those who have access to the secret key can later decrypt it and retrieve it in its original form, called plaintext.
End-to-end encryption is a system where the data is encrypted in a way that only the “ends” (users or their devices) can access the information, and no one else can (people monitoring the network, hackers and not even the service provider). This is in contrast to how most encrypted services work, as we will show below.
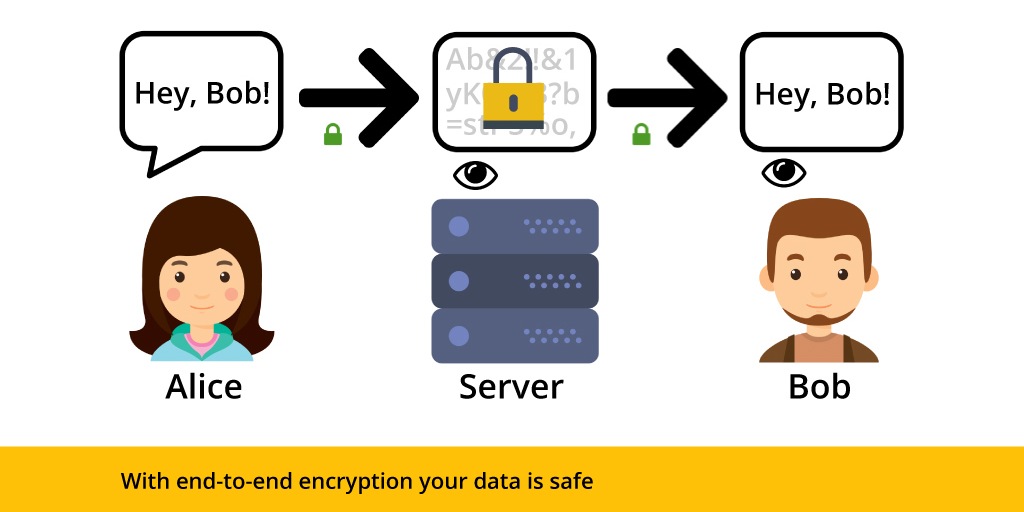
In this example, Alice wants to send a private message to Bob saying: “Hey, Bob!”. Because she’s utilizing end-to-end encryption, her message is encrypted with a key only Bob can access. Since only Bob has access to the key, only Bob can retrieve the original data, and no one else can, not even the service provider.
Why is End-to-End Encryption Important?
The best way to understand why end-to-end encryption is important is to compare it with “regular encryption” (encryption in transit) where data is only encrypted while it’s in transit between the client, and the server can access it in plaintext.
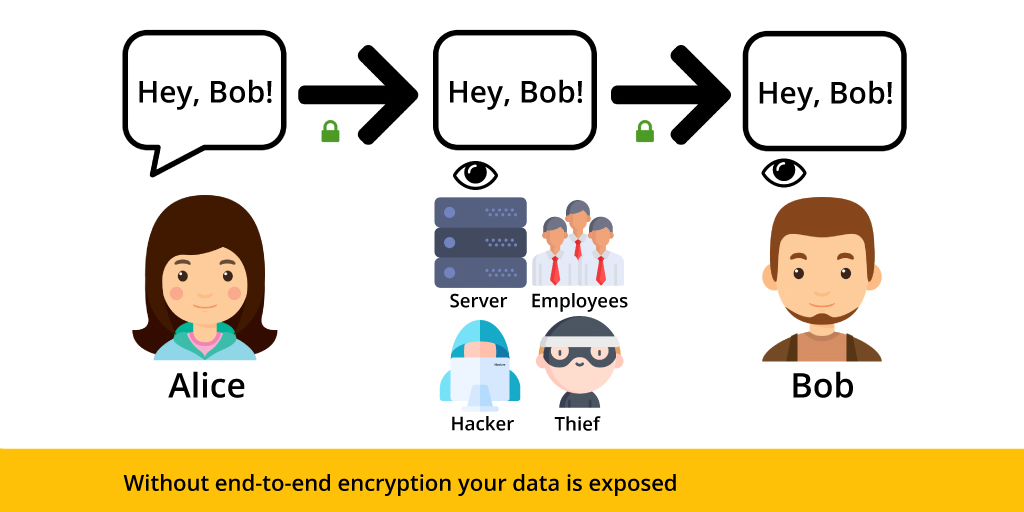
In this example, Alice is sending the same message as before but the data is now only encrypted in transit. This means that the data is encrypted by Alice, then decrypted by the server and encrypted again before being sent to Bob. Therefore, the company running the server has access to Alice’s message, as do all the company’s employees, hackers and other bad actors.
Similar is the case of services implementing encryption at rest. Encryption at rest is the process of encrypting the data before saving it to disk. Since the server has access to the data and the means to decrypt it, encryption at rest doesn’t add much value because it still leaves the data exposed to the server, employees, hackers and other bad actors.
All of these leaks are avoided when using end-to-end encrypted, where only Alice and Bob can access the message in plaintext. The server cannot access it, and neither can the people running it. Even if the server got hacked or improperly accessed, Alice’s information would be safe.
Closing Words
With end-to-end encryption your data stays yours, and yours only. It’s therefore best to use services that employ end-to-end encryption and have it enabled by default (which is not always the case!). Even better, use open-source apps, where everyone can check the source code to verify that an app is as secure as it claims to be. That’s one of the reasons why EteSync is open-source.
But end-to-end is not the whole story, which is why at EteSync we take it one step further. More on that in a future post!
Follow us on Mastodon, Twitter, Facebook or RSS for updates!
The image above uses modified icons by Freepik, Smashicons, Dave Gandy and srip from flaticon.com that are licensed under CC 3.0 BY.

